Table of Contents
- A Brief Introduction to LDAP
- Initial Setup
- ldap-utils and slapd
- Reconfiguring slapd
- Apache Directory Studio
- Managing Users
- Apache
- Common Attributes
- Removing LDAP
- Bibliography
Prerequisite
- Knows how to install Ubuntu desktop on virtual box 🔗
- Proficiency in Linux
- Take a look at my course titled A Beginner's Guide to Linux: Crash Course Edition 🔗
- Basic networking knowledge
- Take a look at my another article titled Linux network commands 🔗
1. A brief introduction to LDAP
The Lightweight Directory Access Protocol (LDAP) is a widely used protocol that offers directory services, such as phone books, addresses, and user accounts [KiDa00].
It is versatile and capable of storing a diverse range of information [NeBr12].
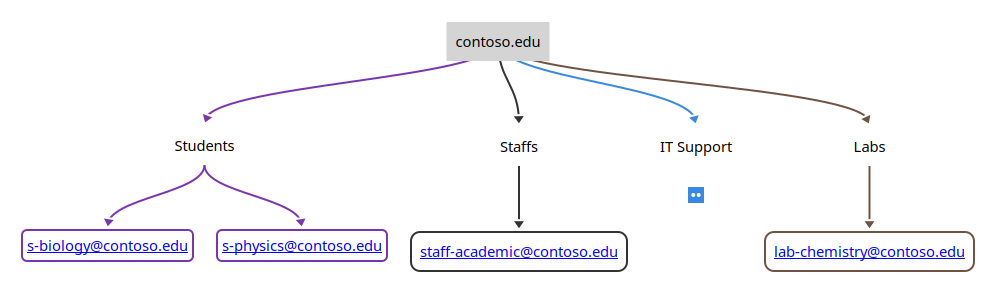
1.1. LDAP as a Tree
The simplest way to visualize LDAP is to perceive it as a tree structure.
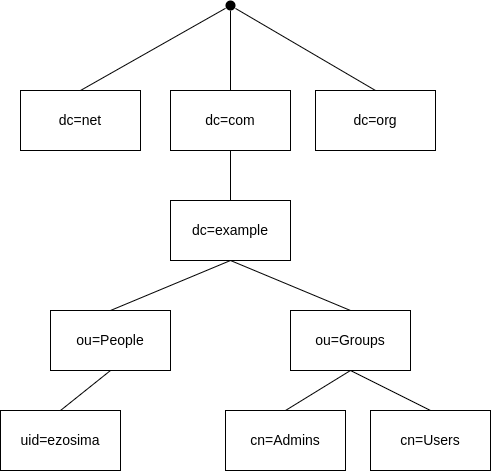
- The first dot represents root.
DCmeans domain component.
DC objects represent the top of the LDAP tree that uses DNS to define its namespace [Ldap00].OUrepresents organizational unit.
It typically holds a group objects or user objects.uidrepresents user's id.
It is an unique identifier.CNmeans common name and represents the name of an entry in the directory.
Distinguised Name
DN in short. It is a unique identifier for an entry in the LDAP directory tree. It includes an object's entire path to the root. Here is an example of DN for the user ezosima:
uid=ezosima,ou=People,dc=example,dc=comSee more of LDAP attributes in the section Common LDAP Attributes Names.
1.2. Difference between Directory and Database
Many people confuse directories with databases. Here are some key differences:
| Directory | Database |
|---|---|
| Directory is designed to read much more. | The Database read and write operations occurs with roughly the same frequency. |
| Directory service is hierarchy in nature. | The data is stored in rows and columns. |
| Directory Services can be concurrently modified in many locations, and if multiple changes occur simultaneously, the last write will overwrite earlier ones. | Data is locked before updating, making sure that there is no simultaneous changes in two locations. |
| The data typically stored in the directory undergoes infrequent changes. | It is designed to handle frequently changing data. |
| The data in the directory is organized hierarchically, and it uses a standard schema for all available applications. | The database is configured on a per application basis, making it suitable for handling complex data models, such as relationships, joins, etc. |
[Chri19], [Cart03], [Maha01]
2. Initial setup
Begin by setting up a VirtualBox instance running Ubuntu Server 22.04.3.
Download the server from https://ubuntu.com/download/server.
After downloading the server, proceed to configure the VirtualBox environment.
Take note of the IP address assigned to the Ubuntu server and we shall call it myldapserver
$ ip addr
192.168.0.79Now, on your "main" machine, let us do couple of things.
Firstly, update /etc/hosts:
$ sudo vi /etc/hosts
192.168.0.79 myldapserverSecondly, copy id_rsa.pub to the myldapserver:
$ ssh-copy-id -i ~/.ssh/id_rsa.pub tux@myldapserver*Replace tux with your myldapserver's actual username.
And attempt to log into the machine using the following command:
$ ssh tux@myldapserver3. ldap-utils and slapd
In this section, I will briefly discuss ldap-utils and slapd.
The ldap-utils package contains several utilities designed for querying an LDAP server [Ldap00].
Slapd, on the other hand, is the stand-alone LDAP daemon. It actively listens for LDAP connections on various ports (default 389), responding to the LDAP operations it receives through these connections [Slap00].
3.1. Moving on to myldapserver
Go to myldapserver and update /etc/hosts:
$ sudo vi /etc/hosts
127.0.0.1 localhost
192.168.0.79 myldapserver.example.com myldapserver3.2. Install ldap-utils and slapd
$ sudo apt install -y ldap-utils
$ sudo apt install -y slapdGive an administrator password:
Administrator password: passw0rdNow, investigate the sockets on myldapserver.
You can observe that port 389 is up and running. LDAP uses tcp 389 for its service [Spee00].
$ ss -ntl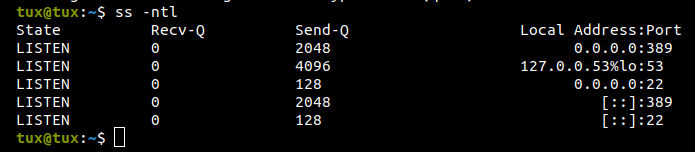
Check if the installation works:
$ ldapsearch -x -LLL -H ldap:/// -b dc=example,dc=com dn
No such object (32)Don't worry if you encounter a "no such object" error; I will explain the meaning of those commands later.
For now, in the next section, let's proceed to reconfigure the LDAP server.
4. Reconfiguring slapd
$ sudo dpkg-reconfigure slapdOmit OpenLDAP server configuration? No
DNS domain name: example.com
Organization name: example.com
Administrator password: passw0rd
Do you want the database to be removed when slapd is purged? No
Move old database? Yes*In a Debian-based distribution, dpkg-reconfigure is used to reconfigure packages after they have already been installed [Ubun00].
$ systemctl status slapdIf it is not active, run:
$ sudo systemctl start slapdNow, try the following steps again:
$ ldapsearch -x -LLL -H ldap:/// -b dc=example,dc=com dnYou must see the following output:
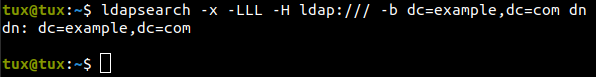
Awesome, let me break down the aforementioned command for you. First of all we are initiating a search request to the LDAP directory from the base DN.
-xindicates the use of simple authentication.-LLLindicates the output result should be in LDIF format without any comments.-H ldap:///specifies the URI of the LDAP server.-b dc=example,dc=comspecifies base DN for the search.dnis the attribute we want to see in the result.
4.1. Create Upper Layers
Now, let's create an upper layer called structure.ldif:
Q. What is .ldif?
The LDAP Data Interchange Format is a standard text format used for representing LDAP objects and LDAP updates (add, modify, delete, modify DN) in textual form [Ibmd23].
$ vi structure.ldifdn: ou=people,dc=example,dc=com
objectClass: organizationalUnit
ou: people
dn: ou=groups,dc=example,dc=com
objectClass: organizationalUnit
ou: groupsAbove, we defined two organizational units (OU) called people and groups.
$ ldapadd -D cn=admin,dc=example,dc=com -f structure.ldif -w passw0rdAnd this command adds the entries from structure.ldif to the LDAP directory.
-Wprompts for bind password.-Dbinds DN.-frepresents file (read operations from the file).
Once again do the ldapsearch:
$ ldapsearch -x -LLL -H ldap:/// -b dc=example,dc=comThe output should be something like:
dn: dc=example,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
o: example.com
dc: example
dn: ou=people,dc=example,dc=com
objectClass: organizationalUnit
ou: people
dn: ou=groups,dc=example,dc=com
objectClass: organizationalUnit
ou: groupsTry to connect myldapserver outside from your virtual box, i.e., "another machine" within the same network, and you should get the same successful results.
another-machine:~$ ldapsearch -x -LLL -H ldap://myldapserver:389 -b dc=example,dc=com*myldapserver or IP address of myldapserver
Now, moving on to the next section on how to use GUI tools like Apache Directory Studio.
5. Apache Directory Studio
Apache Directory Studio serves as a comprehensive directory tooling platform designed for LDAP servers.
Begin by downloading Apache Directory Studio from https://directory.apache.org/studio/download/download-linux.html.
Ensure you have openjdk 11.0.21 installed.
$ java --version
openjdk 11.0.21 2023-10-17If you do not have Java Runtime Environment installed, proceed to install it as shown below:
$ sudo apt install default-jreNow, extract the downloaded Apache Directory Studio:
$ tar xvf ApacheDirectoryStudio-2.0.0.v20210717-M17-linux.gtk.x86_64.tar.gz
$ cd ApacheDirectoryStudio
$./ApacheDirectoryStudio
That's it; it's that simple! 😊
Now,
- Go to File menu > New
- From LDAP Browser, choose LDAP Connection
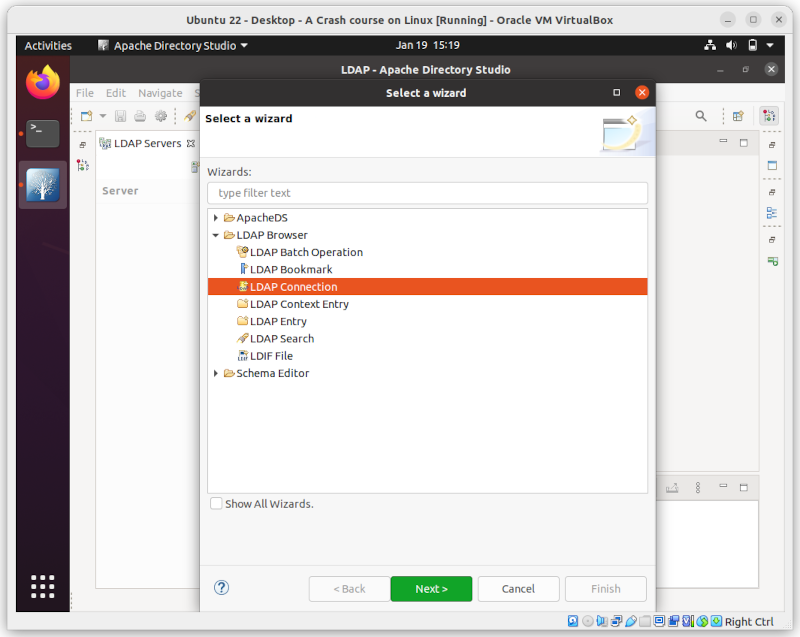
Provide connection details:
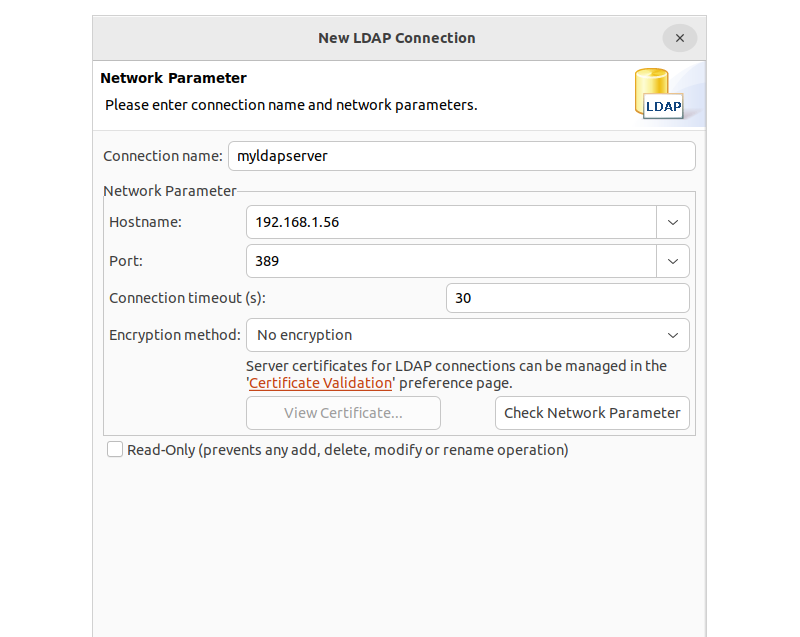
For authentication method, I will be using No Authentication as shown below:
And click Finish. That's it.
Now, you'll notice the Connections tab on the right side of the studio.
Click on "Open connection"

Upon establishing a connection, the LDAP browser will promptly display the Directory Information Tree (DIT).
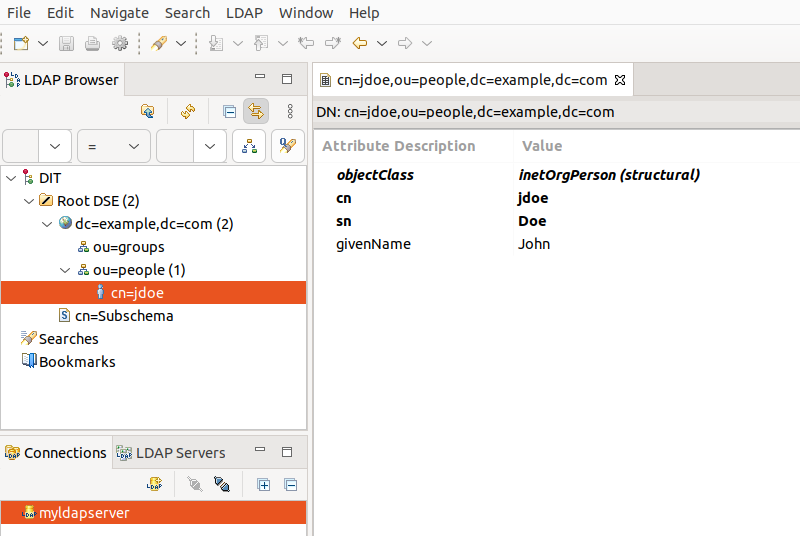
Good! you've just quickly learnt the basics of using Apache Directory Studio.
For a comprehensive user's guide, refer to the Apache Directory Studio documentation available at https://directory.apache.org/studio/users-guide.html.
6. Managing users
In this section, I will guide you through the process of managing users in LDAP. Let's start by creating a user.
6.1. Create an user
To create an user, let us first create .ldif as below:
$ vi user_alexei.ldifPaste the following content:
dn: cn=akaramazov,ou=people,dc=example,dc=com
objectClass: inetOrgPerson
sn: Karamazov
givenName: Alexei
cn: akaramazov
userPassword: Password1$ ldapadd -x -w passw0rd -D cn=admin,dc=example,dc=com -f user_alexei.ldif*-x: means simple authentication
Response:
adding new entry "cn=akaramazov,ou=people,dc=example,dc=com"You can use <<EOF as well as mentioned-below:
$ ldapadd -x -w passw0rd -D "cn=admin,dc=example,dc=com" -a <<EOF
dn: cn=akaramazov,ou=people,dc=example,dc=com
objectClass: inetOrgPerson
sn: Karamazov
givenName: Alexei
cn: akaramazov
userPassword: Password1
EOF- EOF: It stands for "end of file".
6.2. Look the user
To look up the user, use ldapsearch command.
$ ldapsearch -x -H ldap:/// -b ou=people,dc=example,dc=comResponse:
# extended LDIF
#
# LDAPv3
# base <ou=people,dc=example,dc=com> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# people, example.com
dn: ou=people,dc=example,dc=com
objectClass: organizationalUnit
ou: people
# akaramazov, people, example.com
dn: cn=akaramazov,ou=people,dc=example,dc=com
objectClass: inetOrgPerson
sn: Karamazov
givenName: Alexei
cn: akaramazov
# search result
search: 2
result: 0 Success
# numResponses: 3
# numEntries: 2Also, you can use the following command too:
$ ldapsearch -LLL -x -w passw0rd -D cn=admin,dc=example,dc=com -b ou=people,dc=example,dc=comNote: But command shall show you userPassword too.
6.3. Delete the user
To delete the user, enter the following command:
$ ldapdelete -x -H ldap:/// -w passw0rd -D cn=admin,dc=example,dc=com "cn=akaramazov,ou=people,dc=example,dc=com"6.4. Encrypt the password
Now, let's explore the process of encrypting the password for the user kverkhovtsev.
$ slappasswd -s Password1
{SSHA}Kl3qIO0tKIeaux2/DXtFGdUL/fnqB7PlIn this context, the 'slappasswd' command is utilized to hash the password values.
Now, create user_kverkhovtsev.ldif, and paste the following:
$ vi user_kverkhovtsev.ldif
dn: cn=kverkhovtsev,ou=people,dc=example,dc=com
objectClass: inetOrgPerson
sn: Katerina
givenName: Verkhovtsev
cn: kverkhovtsev
userPassword: {SSHA}Kl3qIO0tKIeaux2/DXtFGdUL/fnqB7PlAdd the user kverkhovtsev:
$ ldapadd -x -w passw0rd -D cn=admin,dc=example,dc=com -f user_kverkhovtsev.ldifWhen you ldapsearch the user kverkhovtsev, you will see the following encrypted password in userPassword:
...
cn: kverkhovtsev
userPassword:: e1NTSEF9S2wzcUlPMHRLSWVhdXgyL0RYdEZHZFVML2ZucUI3UGw=6.5. Add a new attribute for the user
Let's add a new attributes initials and description for the user akaramazov:
$ vi user_alexei_add_attributes.ldif
dn: cn=akaramazov,ou=people,dc=example,dc=com
changetype: modify +
add: initials +
initials: Mr. +
-
add: description +
description: The Brothers Karamazov +We will utilize ldapmodify to ensure that our changes are persisted:
$ ldapmodify -x -w passw0rd -D cn=admin,dc=example,dc=com -f user_alexei_add_attributes.ldifYou can cross-check if the user was persisted:
$ ldapsearch -LLL -x -H ldap:/// -w passw0rd
-D cn=admin,dc=example,dc=com
-b ou=people,dc=example,dc=com
"(cn=akaramazov)"
6.5. Modify the attribute of the user
To modify the attribute of the user use replace, as mentioned-below:
$ vi user_alexei_replace.ldif
dn: cn=akaramazov,ou=people,dc=example,dc=com
changetype: modify
replace: description +
description: The Brothers Karamazov Novel by Fyodor Dostoevsky +$ ldapmodify -x -w passw0rd -D cn=admin,dc=example,dc=com -f user_alexei_replace.ldifResponse:
modifying entry "cn=akaramazov,ou=people,dc=example,dc=com"6.6. Delete the attribute
To delete the attribute of the user use delete, as outlined below:
$ ldapmodify -x -w passw0rd -D "cn=admin,dc=example,dc=com" -a <<EOF
dn: cn=akaramazov,ou=people,dc=example,dc=com
changetype: modify
delete: initials
EOFLDAP Authentication in Apache
The design of the directory as an authentication source prioritizes security.
The goal of this section is to demonstrate basic LDAP authorization for the Apache web server.
First, install Apache2 and W3m:
$ sudo apt update
$ sudo apt install -y apache2 w3m*w3m is a text based web browser and pager.
Now, when you browse http://myldapserver, you should be able to see the Apache web server up and running.
Now, this is the page that we want to protect.
Enable the Apache module authnz_ldap:
$ sudo a2enmod authnz_ldapRestart apache2
$ sudo systemctl restart apache2Add the following to the 000-default.conf file:
$ sudo vi /etc/apache2/sites-available/000-default.conf
...
DocumentRoot /var/www/html
<Directory /var/www/html> +
AuthType Basic +
AuthName "Web Site Authentication Required" +
AuthBasicProvider ldap +
AuthLDAPURL "ldap://127.0.0.1:389/ou=people,dc=example,dc=com?cn" +
Require valid-user +
</Directory>
....Check if the config (a2enmod) is working:
$ sudo apachectl configtest
Syntaxt OKFinally, restart apache2
$ sudo systemctl restart apache2Try browsing http://myldapserver, you should be prompted for authentication.

Or, try with w3m from the myldapserver
$ w3m localhost
Username for Web Site Authentication Required: akaramazov
Password for Web Site Authentication Required: Password1By providing the correct credentials, you should be able to view the Apache server-hosted page.
8. Common LDAP Attributes Names
Here are some of the common LDAP attributes:
| Attribute | Description |
|---|---|
| cn | Common name, which contains the name of the object |
| dc | Domain Component |
| o | Name of the Organization |
| ou | Name of the Organization Unit |
| sn | Surname of an individual |
| givenName | First name of the individual |
| uid | User ID, which is unique |
| Email address | |
| c | Country name |
| dn | Distinguished name |
| title | Title |
| url | Other web page |
| company | Company name |
| department | Department name |
| homephone | Home phone number |
| manager | Boss, manager |
| mobile | Mobile phone number |
9. Removing LDAP
To completely remove LDAP from the system, follow these steps:
Stop the slapd:
$ sudo systemctl stop slapdRemove the LDAP packages:
$ sudo apt remove -y --purge ldap-utils slapdRemove the LDAP configuration files:
$ sudo rm -rf /etc/ldap/
$ sudo rm -rf /var/lib/ldap/Delete the user "ldap" and the group "openldap":
$ sudo deluser --remove-home ldap
$ sudo delgroup openldapAnd remove all unused packages automatically:
$ sudo apt autoremoveGreat!
You've just learned the basics of getting started with LDAP.
I highly recommend a couple of resources if you want to dig deeper into LDAP:
- LDAP System Administration: Putting Directories to Work by Gerald Carter
- Linux Network Administrator's Guide: Infrastructure, Services, and Security by Tony Bautts
- https://www.openldap.org/
- https://wiki.debian.org/LDAP/LDAPUtils
- https://ubuntu.com/server/docs/service-ldap
Good Luck!
Articles recommended by the author
10. Bibliography
[Chri19] Christian, “Differences between Directory Services and Databases,” TechDirectArchive, Dec. 18, 2019. https://techdirectarchive.com/2019/12/18/differences-between-directory-services-and-databases/ (accessed Jan. 18, 2024).
[Ibmd23] “IBM Documentation,” May 19, 2023. https://www.ibm.com/docs/en/i/7.3?topic=reference-ldap-data-interchange-format-ldif (accessed Jan. 20, 2024).
[Ldap00] “LDAP Namespace Structure | Understanding Active Directory Services | InformIT.” https://www.informit.com/articles/article.aspx?p=101405&seqNum=7 (accessed Jan. 18, 2024).
[Cart03] G. Carter, LDAP System Administration: Putting Directories to Work. O’Reilly Media, 2003. [Online]. Available: https://books.google.de/books?id=utsMgEfnPSEC
[Ldap00] “LDAP/LDAPUtils - Debian Wiki.” https://wiki.debian.org/LDAP/LDAPUtils (accessed Jan. 20, 2024).
[NeBr12] C. Negus and C. Bresnahan, Linux Bible. Wiley, 2012. [Online]. Available: https://books.google.de/books?id=pdgJ3HIgSHEC
[KiDa00] O. Kirch and T. Dawson, Linux Network Administrator’s Guide. O’Reilly, 2000. [Online]. Available: https://books.google.de/books?id=5bgEyjAtLhEC
[Spee00] SpeedGuide, “Port 389 (tcp/udp),” SpeedGuide. https://www.speedguide.net/port.php?port=389 (accessed Jan. 17, 2024).
[Maha01] V. Mahajan, “Should I Use a Directory, a Database, or Both?,” 2001. https://support.novell.com/techcenter/articles/ana20011101.html (accessed Jan. 18, 2024).
[Slap00] “slapd(8): Stand-alone LDAP Daemon - Linux man page.” https://linux.die.net/man/8/slapd (accessed Jan. 20, 2024).
[Ubun00] “Ubuntu Manpage: dpkg-reconfigure - reconfigure an already installed package.” https://manpages.ubuntu.com/manpages/jammy/en/man8/dpkg-reconfigure.8.html (accessed Jan. 17, 2024).
[Welc00] “Welcome to Apache Directory Studio — Apache Directory.” https://directory.apache.org/studio/ (accessed Jan. 19, 2024).