What is SSH Tunneling?
SSH tunneling is used to securely access private services that are not exposed to the internet.
- It works only over SSH
- It uses port 22 to encrypt and forward traffic
- It can carry other traffic like HTTP, databases, or RDP
Why do we need SSH Tunneling?
Some services are internal only and cannot be accessed directly:
- Databases (MySQL, PostgreSQL)
- Internal web applications
- Admin dashboards
- RDP or SSH on other machines
Exposing these services to the internet would be insecure.
Solution: An SSH tunnel allows access to these internal services through one secure entry point: 👉 SSH (port 22).
Security (encryption)
Some services:
- Don’t encrypt traffic
- Use weak auth
- Were never designed for the public internet
SSH tunnel:
- Encrypts everything
- Hides credentials
- Protects against sniffing
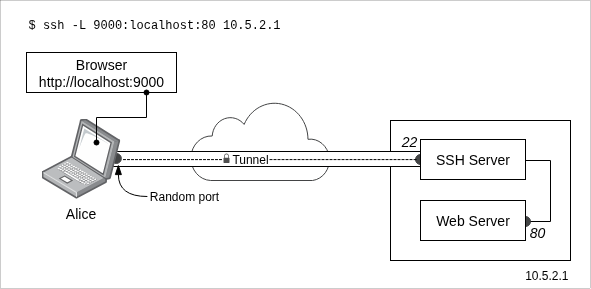
Example
ssh -L 9000:localhost:80 10.5.2.1What happens here?
-
Server
10.5.2.1runs:- SSH (port 22)
- A web service (port 80)
-
Alice:
- Runs the SSH command (
ssh -L 9000:localhost:80 10.5.2.1) - Logs in successfully
- Opens her browser and goes to:
http://localhost:9000
- Runs the SSH command (
-L: Means local port
➡️ This securely connects her to the web service on 10.5.2.1 without server exposing the webservice to the internet.
Difference between SSH login vs SSH Tunneling
| Command | Meaning |
|---|---|
ssh user@ip |
Remote login |
ssh -L / -R / -D |
SSH tunneling (port forwarding) |
Articles recommended by the author
References
- [Neme11] E. Nemeth, UNIX and Linux System Administration Handbook. Prentice Hall, 2011. [Online]. Available: https://books.google.de/books?id=0SIdBAAAQBAJ