This blog post explores the concepts of Access Controls, its policies, models, and more within the domain of Identity and Access Management (IAM).
Table of Contents
- Access
- What are Access Controls?
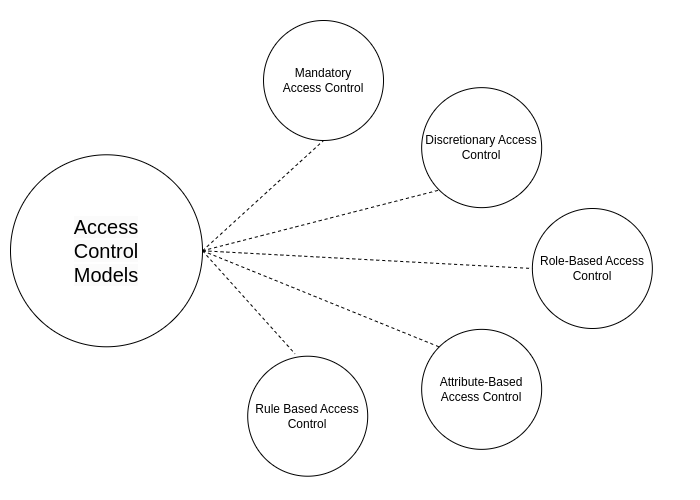
- Models of Access Controls
- Discretionary Access Control (DAC)
- Mandatory Access Control (MAC)
- Role-Based Access Control (RBAC)
- Rule-Based Access Control (RuBAC)
- Attribute-Based Access Control (ABAC)
- Bell-LaPadula Model
- The Principle of Least Privilege
- Bibliography
Access
In simple terms, access is permission to use something. "Something" refers to a resource in the context of security [Rous23]. Allowing access is giving a subject access to a given resource. For example, user Ashish has been granted access to modify the sales.ods file. Conversely, denying access is the opposite of granting access. For instance, user Ashish is not authorized to view the finance.ods file [Andr19].
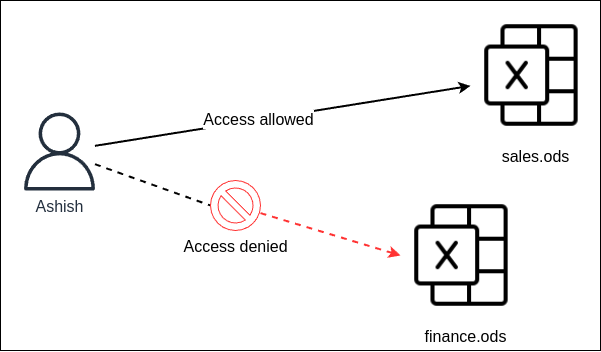
Figure 1. User Ashish has permission to access one file but is denied access to the other file.
What are Access Controls?
Unauthorized access is the most exploited aspect in cybersecurity, as it can result in the compromise of critical assets. Therefore, it's crucial to only permit authenticated users to access a protected resource. Note, authorization is commonly achieved through access controls, which is a fundamental concept in digital identity. Moreover, it primarily deals with policy questions [Wind05].
Let's examine a few examples of access control policies:
- A policy may restrict users to access sensitive data only from the office or office IP address.
- Everyone is allowed to read the 'alpha' folder and its contents.
- All individuals MUST be authenticated to write inside the folder 'beta'.
- The user group called 'sales' is allowed to read/write inside the folder 'delta'.
Models of Access Controls
1. Discretionary Access Control (DAC)
In the discretionary access control (DAC) model, the control of access is based on the discretion of the owner [Harr13]. It is the owner of the file who controls other users' accesses to the file. DAC policies are flexible to implement; however, there are some potential drawbacks to them:
- Information can be moved between objects, so it's hard to assure how information flows in a system.
- DAC policy is vulnerable to Trojan horse attacks [HFKO06].
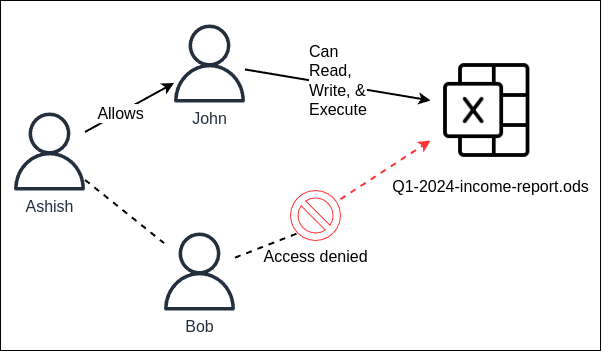
Figure 2. Ashish allows John to access the file while denying access to Bob. This decision is discretionary and only controlled by Ashish.
2. Mandatory Access Control (MAC)
In the MAC policy, decisions are made by a central authority, not by an individual user. MAC-based systems often occur in government organizations. Sensitivity labels, such as "top secret," "secret," "confidential," etc., are applied.

Figure 3. depicts Mandatory Access Control (MAC) as the military classification, based on [Pede17].
3. Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is based on the idea that users are granted access to resources based on their roles within the organization [Wind05]. RBAC is a form of non-discretionary access control, meaning that access control policies are not established at the discretion of the user.
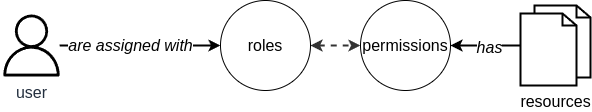
Figure 4. RBAC model.
4. Rule-Based Access Control (RuBAC)
RuBAC allows users to access systems or resources based on a set of predefined rules. For instance, in ACL used by a router, only traffic that comes from source A to destination B on port 80 is allowed [Andr19].
5. Attribute-Based Access Control (ABAC)
ABAC access policies rely on attributes associated with any component of the system, whether it be a user, a resource, or the environment itself. For example, only doctors in the Cardiology department with "Full Access Level" authorization can access detailed cardiology reports for patients. In this scenario, a doctor must possess two specific attributes: firstly, they must belong to the Cardiology department, and secondly, they must hold Full Access Level privileges.
Bell-LaPadula Model
The Bell-LaPadula model provides a clear example of combining DAC and MAC. In this model, entities are categorized into security classification levels such as Unclassified, Confidential, Secret, and Top Secret. The model operates on a fundamental rule known as "No read-up," which means that no user should have the ability to read data at a higher classification level than their own [Olov92].
Moreover, no user should be able to write down to lower classification levels [Andr19].
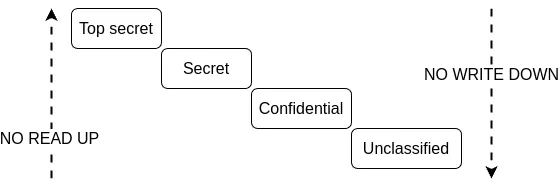
Figure 5. Bell-LaPadula Model based on [Andr19].
The Principle of Least Privilege
To wrap up this article, I would like to talk about The Principle of Least Privilege. This principle is commonly emphasized in computer security. It essentially states that every user and program on the system should only have the minimum necessary privileges to do their job [LeIN04].
Articles recommended by the author
- The Digital Identity Lifecycle
- Identification, Authentication, Authorization, and Accountability in IAM
Bibliography
[HFKO06] V. C. Hu, D. Ferraiolo, D. R. Kuhn, and others, Assessment of access control systems. US Department of Commerce, National Institute of Standards and Technology …, 2006. [Online]. Available: https://csrc.nist.rip/external/nvlpubs.nist.gov/nistpubs/Legacy/IR/nistir7316.pdf
[Harr13] S. Harris, CISSP All-in-One Exam Guide, 6th Edition. McGraw-Hill Education, 2013. [Online]. Available: https://books.google.de/books?id=x-LhdfNs-aAC
[Pede17] T. Pedersen, “CISSP certification: MAC (Mandatory Access Control),” Sep. 12, 2017. https://thorteaches.com/cissp-certification-mac/ (accessed Mar. 18, 2024).
[Wind05] P. J. Windley, Digital Identity. O’Reilly Media, 2005. [Online]. Available: https://books.google.de/books?id=WTmbAgAAQBAJ
[Andr19] J. Andress, Foundations of Information Security: A Straightforward Introduction. No Starch Press, 2019. [Online]. Available: https://books.google.de/books?id=rFmSDwAAQBAJ
[Rous23] M. Rouse, “What is Access? - Definition from Techopedia,” Apr. 07, 2023. https://www.techopedia.com/definition/5413/access-security (accessed Mar. 17, 2024).
[LeIN04] T. E. Levin, C. E. Irvine, and T. D. Nguyen, A least privilege model for static separation kernels. Naval Postgraduate School, 2004. [Online]. Available: https://www.academia.edu/download/48015140/PoLP_SK_NPS-CS-05-003cisr.pdf (accessed Mar. 17, 2024).
[Olov92] T. Olovsson, “A structured approach to computer security,” Chalmers University of Technology, 1992. [Online]. Available: https://core.ac.uk/download/pdf/70597252.pdf