This blog post examines the concepts of identification, authentication, authorization, and accountability within Identity and Access Management (IAM).
Table of Contents
- Identification
- Authentication
- Multi-factor Authentication
- What is Adaptive MFA?
- Mutual Authentication
- Common Tools for Authentication
- Authorization
- Authentication vs Authorization
- Accountability
- Bibliography
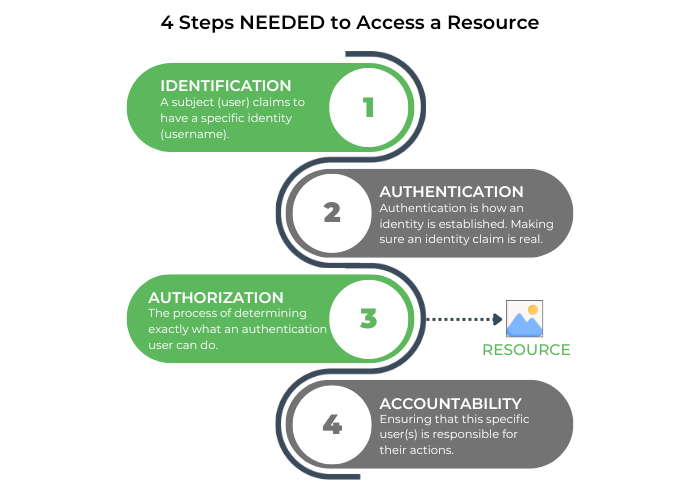
1. Identification
To begin with, identification describes a method by which a subject (user or system) claims to have a specific identity (username or UID). It is assertion of who the subject is.
But what is an identity, exactly?
This question holds significant importance within the realm of IAM. To understand the concept, it's essential to delve into the terminology surrounding identity.
A subject or entity:
- A subject can be individuals, organizations, software agents, or systems that make requests to access resources.
A resource:
- Resources may take the form of websites, items of information, financial transactions, and so forth.
Indeed, identities consist of data concerning a subject. Moreover, figure 1 illustrates this concept.
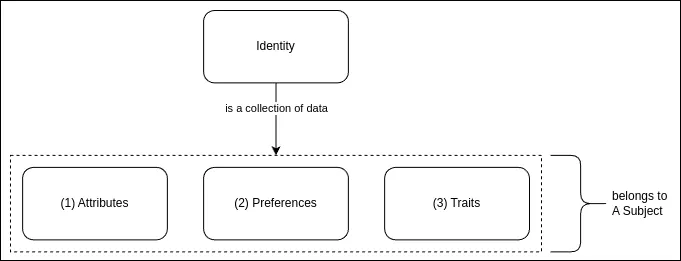
Figure 1. Identity as a collection of data.
Attribute:
Attributes within an identity can include various types of information about a subject, such as medical records, purchase history, credit scores, age, and more.
Also, some attributes may be tied to Access Privileges. For example, Jane Doe holds the job title of Solution Architect; therefore, this job title may be used to provision access for Jane to perform her duties.
Preference:
Preferences represent choices, such as selecting a seat on an airline or choosing an encryption standard.
Trait:
Traits resemble attributes but with a subtle distinction. For instance, a subject's brown eyes would be considered a trait. Traits tend to change at a slower pace.
Therefore, identity is a collection of data about a subject that constitute attributes, preferences, and traits. Having established the definition of identity [Wind05], it's important to note that identity verification differs from authentication. For instance, when you're requested to present an identity card (of any kind), it typically serves for verification purpose rather than authentication [Andr19]. It's important to remember this difference before we talk about authentication.
💡 Extra info: Identity and Personal Identifiable Information (PII) are closely related concepts in data protection and privacy. As mentioned by [Circ16], "PII means information that can be used to distinguish or trace an individual’s identity, either alone or when combined with other information that is linked or linkable to a specific individual".
2. Authentication
Authentication is how an identity is established [Wind05]. It is how we make sure someone's identity claim is real. Authentication is sometimes shortened to AuthN [Msft 24].
There are several factors used for authentication:
(1) Something a person knows
(2) Something a person has
(3) Something a person is
(4) Something a person does
(5) Somewhere a person is
Let's look into one of the each factor:
(1) Something a person knows is commonly referred to as 'authentication by knowledge', which is a common authentication factor. Examples include a password or a PIN code.
(2) Something a person has is commonly referred to as 'authentication by ownership', usually based on a physical possession. Examples include a key, access card, swipe card, mobile phone, badge, et cetera.
(3) Something a person is means authentication by characteristic. The authentication process includes biometrics, which are always unique physical attributes of a person.
(4) Something a person does, this factor is based on the actions or behaviors of a person, which may include analysis of their handwriting and the time delay between keystrokes during typing [Andr19].
(5) Somewhere a person is, is a geographically based authentication factor [Andr19].
2.1. Multi-factor Authentication (MFA)
You may often hear the term "two-factor authentication (2FA)"; it simply refers to combining two of the above-mentioned factors. Moreover, when the above-mentioned factors are combined (multi-factor) and used for authentication, it is considered to be secure. MFA is a security measure [Msft 24] and I highly recommend you to use MFA for the various services you are using.
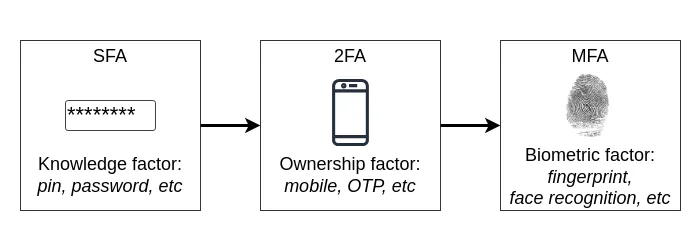
Figure 2. Evolution of authentication factors from SFA to MFA based on [OBMA18].
2.2. What is Adaptive MFA?
Adaptive MFA, on the other hand, is used as an extra layer for protecting digital resources. Adaptive MFA continuously assesses risk factors during authentication processes and may prompt the user for additional verification when required [Auth00].
2.3. Mutual Authentication
Mutual authentication happens when two different parties on a conversation check each other's identity, not just one party. It is also called as "two-way authentication" since the verification process occurs in both directions [What00].
For example, in financial transactions like online banking or shopping online, two different parties verify each other's authenticity for secure and successful transaction.
2.4. Common Tools for Authentication
Now, let's examine common set of tools used for authentication:
A. Passwords
Password is the most common form of authentication. Sometimes referred to as a passcode, it typically consists of a string of characters. Relying solely on passwords for authentication is not considered safe by security professionals.
According to [MaRL13], passwords come in two forms:
- Static Passwords: These remain the same and has high compromise risk
- Dynamic Passwords: These change with each login
Additionally, when a password is the sole method of authentication, it is referred to as Single Factor Authentication (SFA). Remember that passwords are often easy to crack and guess, can be figured out by family and friends, are susceptible to shoulder surfing attacks, and vulnerable to specialized dictionary attacks. Users also tend to forget their passwords or write them down on paper [Brum20].
B. Biometrics

Figure 3. Fingerprint as a biometrics authentication
As mentioned earlier, biometrics fall under the "Something a person is" authentication factor and can be divided into behavioral and physiological approaches.
Behavioral approaches encompass signature recognition, voice recognition, keystroke dynamics, and gait analysis. Physiological approaches include fingerprints, iris and retina scans, hand, finger, face, and ear geometry, hand vein and nail bed recognition, DNA, and palm prints [Weav06].
C. Tokens
Token-based authentication is a protocol which allows users to verify his identity, and in return receive a unique access token [Okta24].
D. Smart cards
Smart card authentication serves as an alternative to passwords. Typically you store your credentials on a smart card in the form of a private key and a certificate.
Whereas, special software and hardware will be used to access them [Redh00].
E. Public Key Infrastructure (PKI)
"PKI authentication can be viewed as a re-usable component that can be integrated with other systems to offer strong authentication, scalability, and mobility particularly for large organizations [HaAb09]".
F. Multi-factor Authentication (MFA)
Refer to the section above.
G. Single Sign-On (SSO)
SSO is the means a user authenticates one-time to a single authentication authority and then access different protected resources without reauthentication [Decl02].
H. Adaptive Authentication
Adaptive Authentication allows a system to dynamically select the best mechanism(s) for authenticating a user depending on contextual factors, for instances location, proximity to devices, and other attributes [ArKB19].
I. Captcha

Figure 4. Google reCAPTCHA
CAPTCHA is a security tool designed to stop bots from certain actions, like signing up or downloading, while still allowing humans to do the same tasks [MoKe15].
J. One-Time Password (OTP)
OTP a temporary and a secure PIN-code sent to the user as 2FA via SMS or e-mail that is valid only for one session.

Figure 5. One-Time Password (OTP)
3. Authorization
Authorization is the process of determining exactly what an authentication subject can do [Andr19]. Authorization is sometimes shortened to AuthZ [Msft 24].
4. Authentication vs Authorization
| Authentication | Authorization |
|---|---|
Shortened as AuthN. |
Shortened as AuthZ. |
| Comes before authorization [Msft 24]. | Comes after authentication [Msft 24]. |
Simply put, authentication is a process of proving a claim to the identity |
Simply put, authorization is granting the authenticated party to do something. |
5. Accountability
Finally, it is important to keep track of activities in the organization, and accountability is tracked by recording user, system, and application activities [Harr13].
This is because any wrongdoing might occur in your organization, and holding someone accountable means ensuring that this specific person is responsible for their actions [Andr19].
Articles recommended by the author
- Digital Identity Guidelines | NIST Special Publication 800-63-3 🔗
- The Digital Identity Lifecycle 🔗
- Access Controls 🔗
Bibliography
[ArKB19] P. Arias-Cabarcos, C. Krupitzer, and C. Becker, “A Survey on Adaptive Authentication,” ACM Comput. Surv., vol. 52, no. 4, Sep. 2019, doi: 10.1145/3336117.
[Auth00] Auth0, “Adaptive MFA,” Auth0 Docs. https://auth0.com/docs/ (accessed Mar. 14, 2024).
[Weav06] A. C. Weaver, “Biometric authentication,” Computer, vol. 39, no. 2, pp. 96–97, 2006, doi: 10.1109/MC.2006.47.
[MoKe15] M. Moradi and M. Keyvanpour, “CAPTCHA and its Alternatives: A Review,” Security and Communication Networks, vol. 8, no. 12, pp. 2135–2156, 2015, doi: https://doi.org/10.1002/sec.1157
[Wind05] P. J. Windley, Digital Identity. O’Reilly Media, 2005. [Online]. Available: https://books.google.de/books?id=WTmbAgAAQBAJ
[Andr19] J. Andress, Foundations of Information Security: A Straightforward Introduction. No Starch Press, 2019. [Online]. Available: https://books.google.de/books?id=rFmSDwAAQBAJ
[Decl02] J. De Clercq, “Single Sign-On Architectures,” in Infrastructure Security, Berlin, Heidelberg, 2002, pp. 40–58.
[What00] "What is mutual authentication? | Two-way authentication.". Available: https://www.cloudflare.com/learning/access-management/what-is-mutual-authentication/ (accessed Mar. 14, 2024).
[Circ16] “Circular No. A-130 - Managing Information as a Strategic Resource.” Office of Management and Budget, Jul. 28, 2016. Accessed: Mar. 21, 2024. [Online]. Available: https://www.cio.gov/policies-and-priorities/circular-a-130/
[Redh00] "Chapter 1. Understanding smart card authentication". Accessed: Mar. 21, 2024. [Online]. Available: https://access.redhat.com/documentation/de-de/red_hat_enterprise_linux/9/html/managing_smart_card_authentication/assembly_understanding-smart-card-authentication_managing-smart-card-authentication
[Msft 24] . "Identity and access management (IAM) fundamental concepts". Accessed: Apr. 12, 2024 [Online]. Available: https://learn.microsoft.com/en-us/entra/fundamentals/identity-fundamental-concepts
[MaRL13] B. Madhuravani, P. B. Reddy, and P. Lalithsamanthreddy, “A comprehensive study on different authentication factors,” IJERT, vol. 2, no. 10, pp. 1358–1361, 2013.
[Brum20] B. Brumen, “System-assigned passwords: The disadvantages of the strict password management policies,” Informatica, vol. 31, no. 3, pp. 459–479, 2020. Available: https://content.iospress.com/articles/informatica/infor408
[OBMA18] A. Ometov, S. Bezzateev, N. Mäkitalo, S. Andreev, T. Mikkonen, and Y. Koucheryavy, “Multi-factor authentication: A survey,” Cryptography, vol. 2, no. 1, p. 1, 2018. Available: https://www.mdpi.com/2410-387X/2/1/1